Mostly Hackers use these methods to hack facebook account, So protect yourself from hackers. In other words, these techniques are generally used by hackers for doing this illegal activity.There are many ways someone can hack Facebook Profile's, and here are the most usual:
1. Phishing/ Tabnapping:
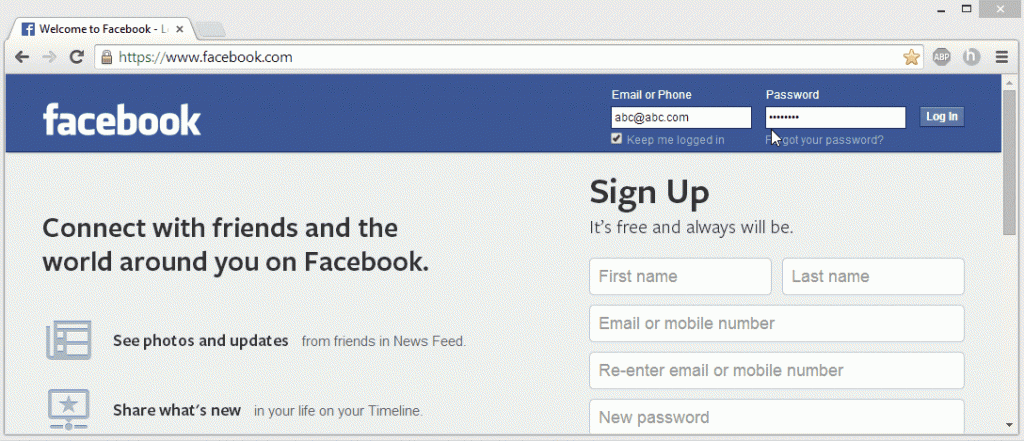
Phishing is still the most popular attack vector used for hacking Facebook accounts. There are variety methods to carry out phishing attack. In a simple phishing attacks a hacker creates a fake log in page which exactly looks like the real Facebook page and then asks the victim to log in. Once the victim log in through the fake page the, the victims "Email Address" and "Password" is stored in to a text file, and the hacker then downloads the text file and gets his hands on the victims credentials. Hacker also create a fake game website and asks user to sign up for play more. If you enter your facebook username and password , that mean you are hack.

How To Avoid Phishing Attacks :
Never Login your Facebook account on other devices
Use Chrome, it identifies the phishing page.
Avoid emails that ask you to log in your facebook account
Avoid signup from facebok account, always use trusted websites.
Avoid spyware and freeware software.
Never play free games on untrusted websites.
2. Keylogging
Keylogging is the easiest way to hack a Facebook password. Keylogging sometimes can be so dangerous that even a person with good knowledge of computers can fall for it. A Keylogger is basically a small program which, once is installed on victim's computer, will record every thing victim types on his/her computer. The logs are then send back to the attacker by either FTP or directly to hackers email address.
How To Avoid Keyloggers :
Always download software from trusted websites
Scan your USB drives for virus
Having a Good antivirus and internet security will avoid keyloggers
3. Saved Passwords Stealer's From Browser:
Almost 80% percent people use stored passwords in their browser to access the Facebook. This is quite convenient, but can sometimes be extremely dangerous. Stealer's are software's specially designed to capture the saved passwords stored in the victims Internet browser.
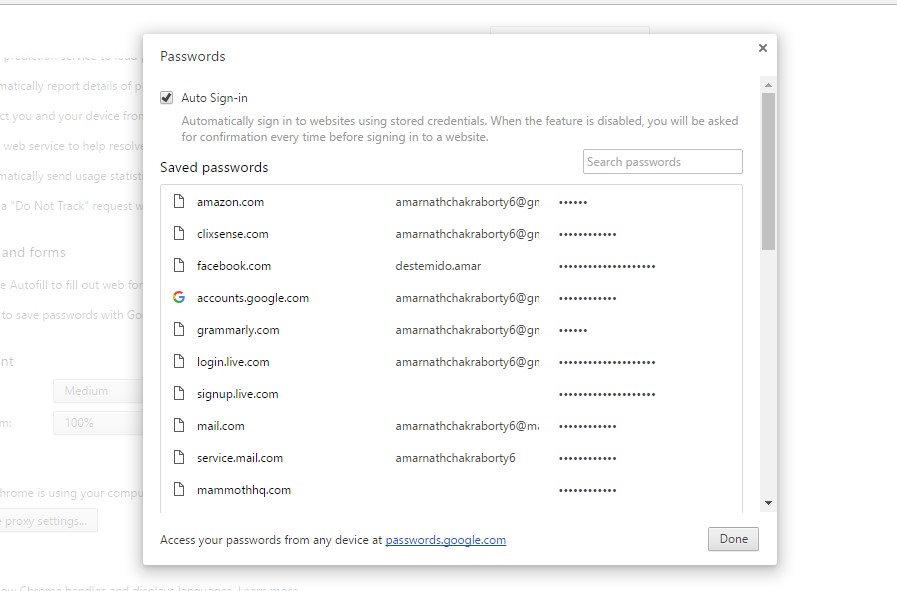 As we all know, whenever we log in with any account in our browser, the browser asks you to save the username and passwords in a computer. Anyone can hack your Facebook accounts from your browser password manager.
As we all know, whenever we log in with any account in our browser, the browser asks you to save the username and passwords in a computer. Anyone can hack your Facebook accounts from your browser password manager.
You can visit this URL and can see username and passwords you saved in your browser
chrome://settings/passwords
How To Protect yourself :
Never save login credentials on your browser.
Always use the strong password on your computer.
4. Session Hijacking:
Session Hijacking can be often very dangerous if you are accessing Facebook on a http (non secure) connection. In Session Hijacking attack, a hacker steals the victims browser cookie which is used to authenticate the user on a website, and use it to access the victims account. Session hijacking is widely used on LAN, and WiFi connections.
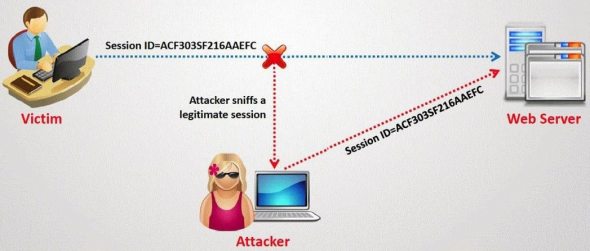
5. Sidejacking With Firesheep:
Sidejacking attack went common in late 2010, however it's still popular now a days. Firesheep is widely used to carry out sidejacking attacks. Firesheep only works when the attacker and victim is on the same WiFi network. A sidejacking attack is basically another name for http session hijacking, but it's more targeted towards WiFi users.
How To Protect yourself :
Avoid leaking cookies over HTTP
Log off websites when you completed the tasks
Avoid open WiFi networks
Use VPN
6. Mobile Phone Hacking:
Millions of Facebook users access Facebook through their mobile phones. In case the hacker can gain access to the victims mobile phone then he can probably gain access to his/her Facebook account. Their are a lots of Mobile Spying software's used to monitor a Cellphone. The most popular Mobile Phone Spying software's are: Mobile Spy, and Spy Phone Gold.
Use a trustworthy mobile security and Antivirus program on your mobile phone.
Never install apps from unknown sources
Uninstall suspicious apps once you notice
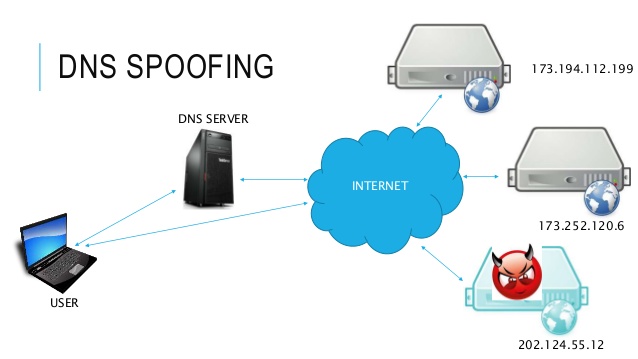
7. DNS Spoofing:
If both the victim and attacker are on the same network, an attacker can use a DNS spoofing attack and change the original Facebook page to his own fake page and hence can get access to victims Facebook account.
How To Protect yourself :
Configure it to be as secure as possible against cache poisoning.
Manage your DNS servers securely
Don’t get caught by known vulnerabilities
Separate the authoritative function from the resolving function using different servers.
8. USB Hacking:
If an attacker has physical access to your computer, he could just insert a USB programmed with a function to automatically extract saved passwords in the Internet browser.
How To Protect yourself :
Insert trusted USB devices into your computer.
Don’t purchase second-hand USB devices
Scan for USB devices once you plugged in
9. Man In the Middle Attacks:
If the victim and attacker are on the same LAN and on a switch based network, a hacker can place himself between the client and the server, or he could act as a default gateway and hence capturing all the traffic in between.
How To Protect yourself :
Use VPN Services
Use Proxy server to access the internet
Use an antivirus that provides best firewall options
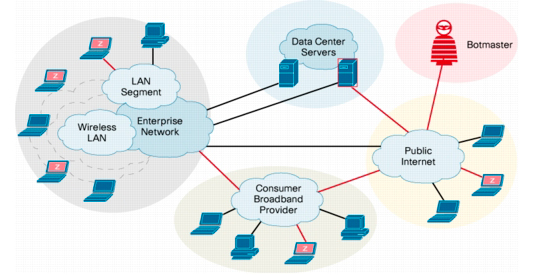
10. Botnets:
Botnets are not commonly used for hacking Facebook accounts, because of it's high setup costs. They are used to carry more advanced attacks. A Botnet is basically a collection of compromised computer. The infection process is same as the key logging, however a Botnet gives you additional options for carrying out attacks with the compromised computer. Some of the most popular Botnets include Spyeye and Zeus.
How To Protect yourself :
Install antivirus and antispyware programs from a trusted source.
Keep all software up to date.
Use strong passwords and keep them secret.
Never turn off your firewall.
Use flash drives cautiously.
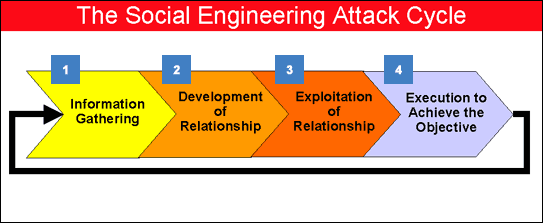
11. Social Engineering:
Social Engineering is simple attack made by hacker, in this method hacker can collect information about victim as much as he can from various methods. If victim uses simple password like his birthday date, mobile number, school name, girlfriend name and bike number , a good hacker can easily guess your password and hack your facebook account.
How To Protect yourself :
Never share personal information via email, your facebook account. chat messenger, phone
Avoid links from unknown or suspicious sites
Blocking USB devices to avoid the risk of Baiting
Never ever write you facebook account in any paper.
Many people use the same password in different websites, my advice is never to use same password for many websites.
#12 Email ID Hacking:
This is the evergreen way to hack Facebook account. The hacker just needs to access the connected email id of any Facebook account and can manually reset your Facebook password
How To Protect yourself :
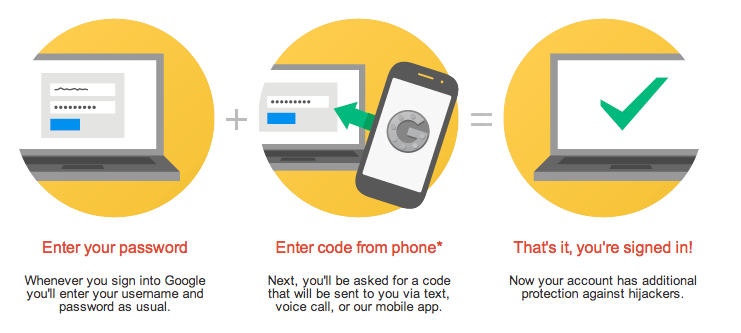
Enable 2 step authentication in your Gmail account
Enable 2 Step authentication in your email account. When you enable this security in your Gmail account, no one accesses your Gmail account without your mobile OTP.
Use strong password in your email.
Never enter email account on unnecessary sites
#13 Viewing Masked Passwords or Source Code:
If your browser saved your Facebook login credentials than any hacker can view your masked passwords (****). Hacker just needs to alter some changes from inspect element in your browser.
To prevent it:
you must never save your Facebook or other Login credentials in Your Browser.
Never leave your PC when it is on the signup page.
#14 Hacking WiFi Network:
There were lots of tutorial on how to hack WiFi network. If you are one of them who use a weak password to setup router security. Then any hacker can hack your WiFi network and hijack all your internet traffic which can let hackers hack facebook account.
How To Protect yourself :
Don’t use Free wifi or public Wifi
If you are using Public wifi, always use VPN
Change your wifi password in regular basis
In Public wifi always use VPN for eencrypt traffic.
Always use WPA-2 security with PIN.
Change your wifi password , if you wifi password has been compromised.
15. RAT:
RAT stands for Remote Administration Tool or RAT (remote access Trojan) . With RAT, a hacker can connect to your PC, without your knowledge. He can see what is going on the screen, what you are currently doing, which sites you surf. It also has the built-in functionality of keylogger.

Hacker can copy files from your Hard disk to his computer, and all this without your knowledge. A good example of RAT is Poison Ivy. It can be customized to connect to your PC on a particular port number specified while creating the RAT.
16. Trojan Horses:
Now these are the most common type of malwares. Trojans spread through warez sites mostly. All of you want free softwares. Right? Beware though! When you download from warez sites, all the keygens and patches and even the original trial programs are trojaned. This means you will get the software for free. But your computer will be affected with a trojan horse.
When you run the patch/keygen, you’ll get the desired output, but in background, your system gets infected with the trojan. Turkojan is a famous Trojan horse. A trojan is much more superior to keyloggers and RATs. It provides much more functions, so that a Hacker has more access to your PC.
There are many other ways which hacker usually uses, for example if you are connected to internet on a LAN, which uses the same router , a hacker can use any packet sniffer and base decoder to read all sensitive data being transmitted from your computer. Cain and Abel is one such sniffer and there are many more.
That’s one reason why I always suggest to enable secure browsing where ever possible. Most of sites like Facebook gives an option to use https login, which encrypts your data and even hacker uses sniffer to capture data, decoding password with those data will not be easy. Brute forcing is another common method, but with technology advancement, most of Email and Web login forms, comes with handling such attack.
How to protect yourself from RAT Trojan Spyware Adware Malware Bloatware :
Install a good licensed anti-virus. I suggest you go for Kaspersky. It’s the best anti-virus out there.
Always have your Windows Firewall turned on.
Never ever trust warez sites. There is a lot of malware flowing out there.
Don’t run .exe programs given by anyone. Trust only yourself.
Never auto-play a pen drive. By this, malware automatically gets installed on your PC.
Don’t run attachments from emails.
If you want to run .exe files safely, run them sandboxed. A free applicationSandboxie is available for this purpose.
If you feel you’re infected, format your PC immediately. No anti-virus can remove a Trojan horse from your PC. It’s very difficult to remove a trojan from an infected PC.
#17 Logout:
Usually, users never log out Facebook account from their computer. It takes just a few seconds to hit the log out button. Anyone can access your Facebook account if you leave your computer while your Facebook account is logged in. Therefore make sure to Logout every time you log in
What Mistakes do we make often?
- Complacent internet habits
- Out of date security and browser versions
- Incorrect Facebook window settings
1. Different passwords:Every single account should have a different password. Never ever have the same password for an insecure site like Facebook and something important like your online banking.
2. Complex passwords:If your password is less than ten characters long, a mixture of upper and lower case letters, numbers and symbols then it is not strong enough. It must never be a name, birthday or information about someone or something around you. An example of a strong password is something like “ca#T_on+M
3. Complex usernames:I bet 95% of you have your email address or name as your username? Bad move rookie. You should make your usernames as complex as your passwords. Many WordPress blogs are set up with the default username of “admin” so hackers are already 50% of the way there. Change your usernames to something complex and unrelated.
4. Updated anti-virus and anti-malware software:You need to have an updated version (or two) of the latest anti-virus and anti-spyware programs. There are free ones like AVG or paid ones like Norton. I also use Malwarebytes (affiliate) to scan for things that anti-virus programs miss. Get one and update it automatically.
5.Latest Chrome, Firefox, Internet Explorer, Safari versions:Don’t just ignore that update request from your browser, do it right away. Some of those updates are security ones. In fact, keep up to date as to which is the most secure browser and just use that. Hello Chrome?
6. Use Facebook and email securely with the right URL:Go log in to Facebook. Go on, do it. Now, does the URL say “http://” or “https://”? If it is the former then you are not in a secure session. Go in to your settings and make sure it always uses https:// and whenever you log into any website make sure you type the “s” if you are logging in.
7. Don’t use public free Wi-Fi:You know when you go to a cafe and log on to the free network? Well, take a look at how easy it is for people to steal your Facebook and email passwords using a simple Firefox plugin. Its really sad that this type of stuff exists. I just don’t use Wi-Fi anymore.
8.Don’t send passwords or store important information online OR offline:Don’t send secure information over the net at all. Especially through chat or email. If someone has got into your account without you noticing they might be monitoring what you are doing. If you need to send passwords to workers, family, etc. then call them on the phone. You should also avoid saving passwords on your hard drive as that too is really easy to access.
9. Make your security questions tough:You know those security questions like “what is your mother’s maiden name?” Well, make them complex answers. For example, in one of mine I selected first pet’s name and then made the answer a complex password. If you ever get hacked you need this information to re-gain access to the account. You don’t want a hacker to change this.
10. Back up everything:You should constantly be backing up your hard drive, emails and blog contents to an external hard drive. If the worst happens and someone deletes your blog content you can get it back up without too much trouble. Imagine if you were relying on a website for your income and it all got deleted?
11. Don’t use your PC Administrator account:Most people use the Administrator account because it gives you freedom to add programs, etc. But, did you know that by using a non-Administrator account you can slow down the spread of a virus attack?
12. Monitor your logged on locations:If you go down to the bottom of your Gmail account you will see a little line of text that says “Last account activity”. This shows you where your account has been accessed from so if you suspect something is not right you should keep an eye on this and record unfamiliar IPs.
13. Use a phishing filter:This can help you identify if anyone is trying to run a phishing scam on you by showing you what is safe.
14. Don’t click links in emails:As a general rule, most banks and financial institutions don’t send you emails with links. Don’t ever click any such email you get. If you genuinely think it is from your bank ring them up instead.
15. Research and read up:Make sure you are up to date with the latest in internet security. You can create alerts in your news reader or follow blogs that update you on such concerns.
Also Read:
Also Read:







0 comments:
Post a Comment